Latest Posts
Commander One Review (2025): Dual-Pane File Manager for Mac
NFC Payments Safe? Tap-and-Pay Transactions
Facebook Account Hacking – Top 5 methods
Local File Inclusion (LFI) Vulnerability: Safeguarding Systems
Finding XSS Vulnerabilty on live website
How to install IDA Free – Installation guide
Rubber Ducky: From Bathtime Buddy to Cybersecurity Powerhouse
Proxy vs. Reverse Proxy: A Detailed Breakdown
Endpoint Detection and Response to Combat Threats
Top 15 Hacking Extensions

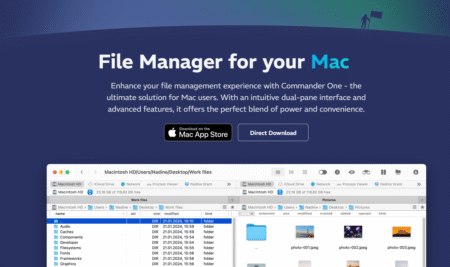
Commander One Review (2025): Dual-Pane File Manager for Mac
Commander One is a dual-pane file manager for macOS, developed by Electronic Team, Inc. It IS designed as an alternative to Finder, giving users more control, flexibility, and features for file management, remote connections, and workflow efficiency. Mac OS needs

NFC Payments Safe? Tap-and-Pay Transactions
You tap your phone, grab your coffee, and go – a simple, convenient NFC payment. But lurking behind that seamless transaction lies a realm of security concerns and questions. Is your tap-and-pay method really safe? Let’s delve into the world

Facebook Account Hacking – Top 5 methods
Are you sure your Facebook account is safe from prying eyes? Think again! Today, we’re diving deep into the world of Facebook security to uncover the surprising vulnerabilities that could compromise your privacy in ways you never imagined. Now, hold

Local File Inclusion (LFI) Vulnerability: Safeguarding Systems
Imagine this: with just one click, your entire system could be exposed to alarming cyber threats. Welcome to the realm of Local File Inclusion (LFI), a hidden peril that demands urgent attention in the digital landscape. In the realm of

Finding XSS Vulnerabilty on live website
The internet is huge, and we spend a lot of time on it. But there’s a sneaky danger hiding there called XXS vulnerability. It’s a problem in cybersecurity, but it affects a lot of websites we use every day. From

How to install IDA Free – Installation guide
Empowering analysts and security researchers, IDA Free stands as a potent tool for analyzing and reverse-engineering binary code. Esteemed among professionals, it garners popularity within the realms of security research and malware analysis. This blog post aims to illustrate the

Rubber Ducky: From Bathtime Buddy to Cybersecurity Powerhouse
Cybersecurity research is a constantly evolving field, demanding innovation and creativity in systematically probing system vulnerabilities. Among the diverse toolkit available, payloads emerge as a critical component in both penetration testing and comprehensive security assessments. In this comprehensive guide, we

Proxy vs. Reverse Proxy: A Detailed Breakdown
Ever wondered about the whispers in the dark corners of the internet? They talk about hidden servers, masked identities, and digital fortresses. But what exactly are these mythical creatures they mention—Proxy and Reverse Proxy? It’s almost like a superhero showdown,

Endpoint Detection and Response to Combat Threats
In today’s interconnected digital world, businesses grapple with an ever-shifting threat landscape. Malicious actors are constantly devising novel and cunning attack methods, making it increasingly challenging for organizations to safeguard their data and systems. This necessitates robust security measures, and

Top 15 Hacking Extensions
In the ever-evolving landscape of cybersecurity, where threats loom at every turn, having the right tools is paramount. While traditional security software plays a vital role, browser extensions add a unique layer of protection and enhancement for both cybersecurity professionals

Third-party Cookies: The Hidden Spies in Your Online Activity
In today’s interconnected world, third-party cookies stealthily collect our digital footprints, painting a detailed picture of our online activities. These tiny trackers, often embedded in websites without our explicit consent, monitor our browsing habits and predict our future behavior. While
The Black Tiger – Installation Guide
Are you ready to take your cybersecurity skills to the next level? Do you want to uncover hidden information with just a few clicks? The Black Tiger, a powerful OSINT tool, is here to make your cyber-investigations more efficient and
Top 10 tools for screenshots in Linux
In the digital world, capturing moments has become second nature to us. Whether it’s a vital piece of information or a casual encounter online, screenshots play a crucial role in preserving our digital experiences. However, when it comes to Linux,
Top 10 Tools for Securely Deleting Files on Windows
In today’s digital age, safeguarding your personal and private data is more crucial than ever. When it comes to Windows, there’s a plethora of free tools available to ensure the secure and permanent deletion of files from your device. Let’s

Top 10 Tools to handle ZIP/RAR files on MacOS
In the daily hustle of dealing with numerous files and documents, managing different extensions on Mac devices can be quite challenging. Often, we encounter files in .rar or .zip formats, making bulk sharing a bit cumbersome. Fear not, Mac users!
Top 10 Tools to Handle ZIP/RAR files on Windows
When navigating through the labyrinth of files on our laptops or desktops, the fear of accidental deletions or misplaced data always looms. While keeping track of every piece of information is nearly impossible, safeguarding files can be efficiently achieved through
Top 10 Tools to make a bootable Pen Drive
In the bygone era of CD and DVD burning procedures, installing or rescuing a system felt like a marathon. The time-consuming process and memories of dealing with CD and DVD writers are now buried with the advent of flash drives.
Mastering Mac: The Ultimate Top 10 Ad Blocker Tools
In our fast-paced world, the Internet has become the ultimate source of entertainment, information, and productivity. Whether you’re catching up on your favorite shows, studying for exams, or resolving burning questions, the internet is your go-to companion. However, the constant
Top 10 Tools to Securely Erase Data on Mac Devices
In the digital age, safeguarding your data is paramount. While Apple provides a secure environment for its users, the need to permanently erase sensitive files remains crucial. Enter the realm of file shredders – specialized tools designed to obliterate data
Top 10 Websites to check if your account has been compromised
In the digital realm, where information is gold, the security of your online accounts is paramount. Unauthorized access, data hacks, and compromised credentials have become daily threats. As cyber threats evolve, it’s essential to stay one step ahead. We’ve curated
Top 10 Video Players for iPhones
In a world dominated by online streaming platforms, the traditional joy of watching videos on iPhones should not be overlooked. iPhone users crave a video player that not only delivers crisp visuals from their devices but also seamlessly integrates with
Top 10 video players for Mac
In a world dominated by digital advancements, videos have become an integral part of our lives, serving purposes beyond mere entertainment. Whether for educational endeavors or professional tasks, the need for a reliable video player is paramount. This holds true

How to Stop YouTube Anti-Adblocker Pop-Up (2023)
YouTube is a great platform for watching videos, but the ads can be annoying. That’s why many people use ad blockers to prevent ads from playing. However, YouTube has recently started implementing anti-adblocker measures that can prevent users from watching
Top 10 tools to handle ZIP/RAR files on iPhones
Dealing with files can be a daily struggle, especially when it comes to managing compressed files like RAR and ZIP. These file formats, designed for efficient data compression and storage, play a crucial role in safeguarding data and reducing file
Top 10 Tools For Videos on Linux
In the era of online streaming dominance, having a reliable video player for both online and offline viewing on Linux becomes paramount. While subscription-based streaming platforms abound, open-source free applications offer an efficient alternative for users seeking flexibility and effectiveness.
Top 10 Android Ad Blocker Tools
In today’s internet-centric world, where we find entertainment, education, and answers to our queries online, ads often sneak in as uninvited guests. Picture this: You’re deeply engrossed in the climax of your favorite movie or solving a critical problem, and
Top 10 Dropbox Alternatives
When in the present world most of the data is stored in soft copies it becomes immensely important to have a large amount of space in your devices to store them. In such problems, Dropbox comes as an amazing option
Top 10 Github Alternatives
GitHub, a web-based interface utilizing Git, has been the go-to place for hosting open-source projects, fostering collaboration among multiple users. However, with Microsoft’s acquisition of GitHub, the landscape has shifted, prompting users to explore alternatives. This guide delves into the

SQLMap: Your Comprehensive Guide to Database Security Testing
In the ever-evolving landscape of cybersecurity, staying one step ahead of potential threats is paramount. Web applications, in particular, are susceptible to vulnerabilities that can compromise the security of your data. Enter SQLMap, a powerful and open-source penetration testing tool

HTTrack: Your Easy Guide to Web Scraping
In the ever-expanding digital landscape, the capacity to capture and archive web content is an invaluable asset. Enter HTTrack, a potent, open-source web scraping tool that empowers you to take control of web data. In this in-depth exploration, we’ll delve
Top 10 Google Drive alternatives
In the present digital age, where the majority of our data exists in the form of soft copies, having ample space on our devices becomes crucial. Cloud storage services like Google Drive have played a pivotal role in enabling us
Top 10 Hidden camera detector apps for android
Cameras have become an integral part of our daily lives, capturing precious moments and adding a glow to our faces after a long day. However, with the rise of malicious intent, the fear of hidden cameras tracking our every move

WPScan: Unmasking WordPress Vulnerabilities
In the dynamic realm of web content management systems, WordPress undeniably reigns supreme. However, with great popularity also comes the substantial responsibility of safeguarding your WordPress website against potential threats. Enter WPScan: an indispensable open-source security tool that excels at

Dirbuster: Your Guardian Angel in the World of Cybersecurity
Cybersecurity has become a battlefield, and every organization is arming itself with powerful tools to protect its digital assets. In this relentless struggle, a tool named Dirbuster stands out as a formidable weapon. In this blog post, we will dive
Hash-Identifier Guide: Features, Uses, and Commands
Are you ready to explore the depths of Hash-Identifier? In this comprehensive guide, we’ll dive deep into the features, uses, and commands of this powerful cybersecurity tool. Whether you’re a seasoned professional or a curious learner, this guide will equip
Top 10 Hidden Camera Detector Apps for iPhone
Cameras have become an important part of our day-to-day life let it be capturing your precious moments or taking a selfie after a long working day brings a separate glow to your face. But like all other useful inventions, it
Top 7 Linux Ad Blocker Tools
In today’s digital era, the internet has evolved into our primary source of entertainment and information. Whether we’re enjoying our favorite shows, studying from popular sites, or searching for answers to our queries, the internet plays a pivotal role in

OWASP-ZAP: Your Shield Against Cyber Threats
Are you ready to dive into the thrilling world of cybersecurity, where you can become the hero who saves the day? Well, let’s take the plunge and introduce you to OWASP-ZAP, your trusty sidekick in the fight against digital villains!

SkipFish: Ultimate Weapon Against Cyber Threats
Are you tired of feeling defenseless against the ever-evolving landscape of cyber threats? Do you wish there was a tool that could give you an upper hand in identifying vulnerabilities and securing your systems? Look no further, as we introduce
Top 7 iPhone Ad Blocker Tools
In today’s digital age, the internet serves as our primary source of entertainment, education, and information. From watching movies to studying, the internet plays a crucial role in almost every aspect of our lives. However, the incessant intrusion of annoying
Top 10 Tools for Securely Deleting Data on Android
Deletion of data remains a significant concern for mobile users, be it on Android or iPhones. In this fast-paced technological era, data security is crucial, making it vital to safeguard and securely dispose of data when not in use. Data
Top 10 Cooling Apps for Android (Overheat issues Solved)
In the fast-paced world of technology, dealing with overheating issues on your Android device can be a real headache. From draining your battery to stressing out your device’s CPU, overheating is not only annoying but can also impact your device’s
Top 10 Tools to handle zip/rar files on android
Dealing with archived and compressed files is a daily affair, and it becomes even more crucial when you’re navigating the world of Android devices. Zip and RAR files are commonplace, but handling them efficiently on Android can be a bit

Fluxion: Unmasking Wi-Fi Secrets
Are you ready to delve into the intriguing world of Wi-Fi hacking? Well, Fluxion, the powerful tool within the Kali Linux arsenal, is your passport to unlocking the secrets of wireless networks. In this comprehensive guide, we’ll not only navigate
Top 10 Tools for SMS on Android
In the era of instant messaging apps like WhatsApp and Telegram, the traditional Short Message Service (SMS) may seem overshadowed. However, for Android users, the world of texting holds a variety of options beyond the default messaging app. Let’s explore

FinDOM-XSS – Guide to Master Detection and Mitigation
In a digital age where web application security is of paramount importance, one tool stands out as a formidable ally in the fight against Cross-Site Scripting (XSS) vulnerabilities. FinDOM-XSS, with its speed, simplicity, and powerful capabilities, is your key to

Lynis Mastering: Your Ultimate Kali Linux Cybersecurity Tool
Are you ready to dive into the fascinating world of cybersecurity? Brace yourself because today, I’m about to unravel the secrets of a powerful tool called Lynis, which will change the way you perceive and protect your systems. Whether you’re

Instagram and Teens: Guide for Parents to Safeguard Their Kids
As a parent in the digital age, you’re likely concerned about your teens’ safety on social media platforms like Instagram. While Instagram provides a platform for creativity and socialization, it also comes with a slew of potential risks. In this
Cyberbullying: Where to Report, How to Protect, Overcome & More
In today’s interconnected world, the internet has transformed into both a blessing and a curse. While it allows us to stay connected, learn, and work remotely, it has also become a breeding ground for a dark and unsettling phenomenon known
Top 10 Screenshot Tools for Mac
Screenshots, those digital keepsakes, play a crucial role in our tech-driven lives. Mac users, however, often grapple with the intricacies of capturing their screen. Fear not! This article unveils the top 10 screenshot tools, ensuring a seamless and efficient experience

Child’s Identity Theft: How Do I Keep My Kids’ Personal Data Safe?
Is Your Child’s Identity at Risk? Learn How to Safeguard Their Personal Data Now! In today’s digital age, where technology and the internet are an integral part of our lives, protecting ourchildren’s personal information has become more crucial than ever.

Cybersecurity Career Guide: A Journey from Novice to Expert
Are you intrigued by the mystique of the digital realm, the thrill of outsmarting hackers, and the relentless pursuit of safeguarding sensitive information? If so, welcome aboard, aspiring cyber defender! I’m here to take you on a gripping journey through

Fileless Malware: Can I Be Hacked Without Any Interaction with an Unknown File?
One click could change everything. Just one, seemingly harmless click. We often think we’re safe from the clutches of cybercriminals if we avoid sketchy websites and don’t download suspicious files. But what if I told you that “Fileless Malware” can

SIM Swap Scam: What it is and How to Protect Yourself
🚨 Don’t be the Next Victim! Learn How to Shield Yourself Against the Silent Threat of SIM Swap Scams 🚨 In the vast digital realm where convenience and vulnerability coexist, there’s a lurking menace that has swindled countless individuals out

What to Do If You Receive a Data Breach Notice: My Personal Survival Guide
One Click Away from Disaster: How I Navigated the Storm of a Data Breach Notice We’ve all been there, right? That unsettling moment when you receive an email notification titled “Data Breach Alert.” It was just another mundane day when

Gamers Should Prioritize Online Safety: 10 Tips to Stay Secure
Attention, fellow gamers! In the electrifying realm of online gaming, where every click is a step towards victory, and every second counts, you’re not just battling virtual foes; you’re fighting off real-world threats that could jeopardize your gaming paradise. From

How to Recognize and Defend Against Vishing Scams
As technology continues to advance, so do the tactics of cybercriminals seeking to exploit individuals for their personal and financial information. One such tactic that has gained prominence in recent years is vishing, a portmanteau of “voice” and “phishing.” Vishing

How to spot a Fake Mobile App – 10 Tips
The widespread use of mobile technology has revolutionized the way we perform various tasks, from shopping and banking to entertainment and productivity. Mobile apps play a central role in this ecosystem, providing us with convenient access to services and information.

Twitter Charges for SMS 2FA: Protect your account in this New Era for Free
In the digital realm, where personal data and online interactions are increasingly valuable commodities, ensuring the security of your social media accounts has never been more crucial. Recently, Twitter (currently “X”) made a significant announcement that left many users pondering
Steam account hacked? Follow this steps to recover in back
In today’s digital age, online security is paramount. Your Steam account, which holds your valuable gaming library, in-game items, and personal information, is no exception. Discovering that your Steam account has been hacked can be a distressing experience, but don’t
How to recover hacked Instagram account?
Is your Instagram account hacked? Stay calm – here’s how to get your account back and how to avoid getting hacked (again). In the age of social media dominance, Instagram stands as one of the most popular platforms for sharing
The Evolution of Blockchain: Part 2
Having established a foundational understanding of blockchain technology in our previous segment (Blockchain Fundamentals) , let’s now delve even deeper into its transformative impact across various sectors. Our journey takes us directly into the heart of blockchain’s potential, thereby unveiling
Windows Login Screen Hacking: Revealing How Hackers Bypass Security
In today’s digital era, cybersecurity holds unparalleled significance. Our computers frequently safeguard our personal and sensitive data, relying on passwords and various security protocols. The forefront defense against unauthorized entry manifests as the Windows login screen, demanding users provide their

Ensuring Security in WordPress 101
In today’s digital age, where online presence has become synonymous with success, websites serve as a gateway to businesses. Among the numerous platforms available, WordPress remains a popular choice. Thanks to its user-friendly interface, extensive plugin ecosystem, and customizable themes.

Legal and ethical considerations in OSINT investigations
In today’s digital age, Open Source Intelligence (OSINT) has emerged as a powerful tool for gathering information. However, conducting OSINT investigations requires investigators to navigate a complex landscape of legal and ethical considerations. In this advanced-level blog, we will delve

Beef: An Essential Kali Linux Tool for Advanced Penetration Testing
In the realm of cybersecurity and penetration testing, Kali Linux has emerged as a go-to operating system. Its extensive range of tools enables professionals to identify vulnerabilities and secure systems effectively. One such powerful tool that stands out in the

Mastering Maltego: A Comprehensive Guide
In the ever-evolving landscape of cybersecurity and threat intelligence, the ability to access comprehensive and reliable information is paramount. Gathering and analyzing data from various sources can be a complex and time-consuming task. However, tools like Maltego have emerged to

Exploring the Power of Nikto: A Comprehensive Guide
Nikto, an open-source web vulnerability scanner, is an indispensable tool for security professionals and ethical hackers alike. In this guide, we will delve into the features, functionalities, and practical applications of Nikto. By the end, you’ll be equipped with the
Tools To Combat Remote Work Vulnerability
In the wake of the COVID-19 pandemic, remote work has undeniably become the new norm for many organizations around the world. While this shift has undoubtedly brought about increased flexibility and productivity, it has also significantly exposed companies and their

Increased Attacks on Cloud-Based Services: A Growing Concern
In recent years, the adoption of cloud-based services has soared, revolutionizing the way individuals andorganizations store and access their data. The cloud offers unparalleled convenience, scalability, and cost-effectiveness, making it an attractive choice for businesses and individuals alike. However, this

Authentication Evolution: The Progress of Multi-Factor Security
In today’s interconnected digital landscape, safeguarding personal information and sensitive data has become paramount. Traditional passwords alone are no longer sufficient to protect against sophisticated cyber threats. To address this challenge, the concept of multi-factor authentication (MFA) has emerged as

Beware of Pegasus: Safeguarding Your Digital Privacy in the Modern Era
Introduction In today’s interconnected world, where technology governs our lives, the digital landscape has both its wonders and its dangers. One of the most notorious threats that has emerged in recent times is the Pegasus spyware. In this blog, we

What are The Best Cybersecurity Measures in 2023?
Cybersecurity must be your primary goal in 2023 because there’s an influx of hacking attempts. The prime target is data breaches, and there’s an unprecedented increase in automotive hacking due to the introduction of autonomous vehicles. So, the question is

How To Read My Wife’s Text Messages Without Her Knowing?
Privacy and personal space between spouses are always mandatory. However, there are instances when you need to look into your partner’s chat history to see if they are safe from social media threats and harassment. Besides, you may also need

Dark-Web: Exploring the Unknown
The Dark-Web is often portrayed as a sinister and shadowy world, home to criminal activity and illicit trades. While it’s true that the Dark-Web has been linked to some heinous crimes, it’s not all doom and gloom. In fact, there

Investigating cybercrime with OSINT
As the world becomes increasingly digital, the threat of cybercrime continues to grow. Criminals are using ever-more sophisticated methods to steal data, infiltrate systems, and disrupt online activity. Investigators need to equip themselves with the latest tools and techniques to

Tools and Techniques for OSINT
Open-source intelligence (OSINT) is the practice of collecting and analyzing information from publicly available sources to gather intelligence. Online investigations using OSINT can be used for a wide range of purposes, such as investigations into cybercrime, due diligence investigations, and

Phone-Number OSINT: Revealing Hidden Information
Phone Number OSINT, or open-source intelligence gathering using phone numbers,has become an increasingly popular technique for gathering valuable insights about an individual. With the widespread use of smartphones and the internet, phone numbers have become a key identifierthat can be

The World of People OSINT
Peering Behind the Curtain : The World of People OSINT In today’s digital age, the internet is awash with information about people. Countless sources of information exist that people can use to gain insight into a person’s life, ranging from

IP-Address OSINT – Unlocking the Secrets
In today’s interconnected world, online threats are becoming more and more sophisticated. Investigating and combating cybercrime requires a range of techniques and tools, one of which is IP-Address OSINT. This powerful technique involves using open source intelligence to gather information

Unveiling the Power of Domain-Name OSINT
Introduction The rise of the internet and digital technology has brought about a new age of criminal activity, with cybercrime becoming a major threat to individuals, businesses, and governments worldwide. In this digital landscape, it is essential for investigators to

Illuminating DarkWeb Investigations with OSINT
The dark web is a hidden part of the internet that is not accessible through regular search engines or browsers. It is often used for illegal activities, such as drug trafficking, human trafficking, and cybercrime. However, it can also be

Image OSINT: Unleashing Image Intelligence
In today’s digital age, images play a significant role in our lives, and they can also be a valuable source of information. Image OSINT (Open Source Intelligence) is a powerful tool that can help you extract valuable information from images

Email OSINT: Investigate Efficiently
Emails are one of the most widely used forms of communication in today’s digital age. Whether it’s for personal or professional reasons, people rely on emails to exchange important information. However, email can also be used for nefarious purposes, such

Social Media OSINT
Understanding and Investigating Social Media Profiles with OSINT The widespread use of social media has brought about significant changes in how people communicate, socialize, and share information. While social media platforms offer many benefits, such as staying connected with friends

Getting Stated with OSINT
Open Source Intelligence, or OSINT, is the process of collecting information from publicly available sources to support decision-making processes. OSINT is used by intelligence analysts, law enforcement agencies, investigators, and journalists to identify potential threats,investigate crimes, conduct due diligence, and
Emerging Cyber Threats
The threat of cyber attacks is growing as we become more dependent on technology and the internet. Emerging cyber threats are constantly evolving, becoming more sophisticated and unpredictable, making it increasingly difficult to protect our digital assets. It’s essential for
Quantum Computing: Past, Present, and Future
Quantum computing is an emerging technology that has the potential to revolutionize many industries, including cybersecurity. In this blog, I’ll discuss about the origin of quantum computing, how it has affected the current scenario, and its future. Additionally, I’ll also

Social Engineering Attacks
Social engineering attack is a type of cyber attack that uses psychological manipulation to trick individuals into divulging sensitive information or performing actions that benefit the attacker. These attacks can be incredibly effective, and their consequences can range from stolen

Blockchain Fundamentals – Part 1
Blockchain technology has become a buzzword in recent years, but many people are still unclear about what it is and how it works. In this blog, we’ll explore the basics of blockchain and how it has transformed the world of

Zero-Day Exploits: The Hidden Threat to Cybersecurity
In the world of cybersecurity, zero-day exploits have become a buzzword, often associated with high-level attacks and sophisticated hacking campaigns. But what exactly is it and how do they work? This blog post will explore and discover the process of

Steganography: Hiding Secret Files using openstego
Do you have sensitive information or files that you want to keep hidden from prying eyes? If so, you may want to consider hiding them within your music and photo files.With this technique, you can protect your confidential data and

RAM Forensics: Is your PC hacked?
With the increasing number of cyber attacks, it’s becoming increasingly important to know whether your computer has been hacked. One of the best ways to determine if your computer has been compromised is to perform a RAM forensics analysis. In

Windows Security – Are you safe using it?
Remember when Norton, McAfee, and Webroot ruled the world and we were all buying separate antivirus software for our computers? These days, many of us have forgotten about these products and instead opt for the built-in protection which is provided

Top 10 Ethical Hacking Tools
In this blog, I’ll be guiding and briefly explaining the top 10 tools used by hackers. Hackers do not prefer any Windows-based system for hacking, they prefer Debian-basedLinux system, which is developed for penetration testing and digital forensics, specifically Kali

Fighting a ransomware attack: a comprehensive guide
In this blog, I’ll show you how to defend against a ransomware attack and how to protect your system from ransomware attacks. What is a Ransomware Attack? A ransomware attack can be defined as a malware attack where the attacker
How to hack anyone using an image
In this blog, I’ll be discussing “How you can hack and take control of any computer, just by using an image.”So generally, when you are given an image, you don’t really think, “What could happen if I open this image?

NMAP – To Find Network Vulnerabilities
In this blog, I’ll discuss NMAP, which is a free and essential tool for hackers and pretty much anyone in IT. NMAP is a network scanner created by Gordon Lyon. NMAP is used to discover hosts and services on a computer network by transferring packets and analysing the responses. We can scan the entire network,

The Ethics of Keyloggers – Everything you need to know
In this blog, I’ll be explaining about a keylogger that I’ve created using Python. I’ll be explaining the full Python code in details and will also show how it works and what all implementations can be done in that tool.

Finding information about our target using Gmail – Gmail OSINT
In this blog, I’ll explain how to extract any user’s information simply by his or her Gmail address.Nowadays, Gmail is the only e-mail service that 99% of people rely on. The term “OSINT,” or “open source intelligence,” means extracting information

5 Best Hacking Devices – 2022
Hacking is the process of using various types of tools or technology in the form of computer programmes and scripts to get access to unauthorized data to test the security measures of a computer system or network.Hacking devices are simply

Paraphrasing Technology To Boost Marketing Campaigns In 2022
Technology is advancing, and paraphrasing is one of them. So, how does it boost your marketing campaign? It was in 1996 when Bill Gates said content is king. Now, think about the foresight of the Microsoft chief and how he

Most Effective Tips for Your Mobile App Security
The number of smartphone users has been increasing every year across the globe. As a result, every business has to launch mobile applications to bring more convenience to their customers. Apart from delivering goods and services, companies also use mobile

Wi-Fi Speed Upgrade: Make Your Internet Faster with These Tips
Even if you have subscribed to the fastest internet plans, you still need help maintaining the fastest internet possible for all your devices. Of course, the first thing you need to do is make sure you have an internet connection

How to Learn the Latest Cyber Security Techniques?
Preventing hostile assaults on internet-connected systems such as computers, websites, mobile devices, communications devices, networks, and data defines cybersecurity. It involves safeguarding data, applications, networks, and procedures, encompassing technology that includes systems, networks, programs, and data. Security in this realm

Fintech: Innovation and Transformation in Financial Industry
The financial industry has long been the engine of innovation, prosperity, and globalization. But the industry is changing rapidly, with innovations such as mobile payments, blockchain technology, and new payment systems. It will be transformational for finance to survive in

Why Every Business Needs a Cybersecurity Plan in 2022
Most managers would consider a robust cybersecurity plan to be an essential part of business operations. Protecting your trade secrets and your customers’ data is at the core of your responsibilities as a business. However, many small and medium-sized businesses

Does VPN affect your router?
Almost everyone uses VPN now on a daily basis. Some people want to remove restrictions from the content, while some of them want to ensure security. However, one of the main questions that may come to your mind is whether

Basics of Dynamic Application Security Testing Tools
Dynamic Application Security Testing (DAST) is a security testing technique that has been used by major corporations and organizations to secure their GCP cloud infrastructure. Dynamic means that the tests are performed in an automated manner, unlike other software testing
Top 10 Wordlists for Pentesters
In this tutorial, we will see some of the best wordlists for pentesters. A pentester is professional in cracking password, stressing authentication panels or even a simple directory Bruteforce it all drills down to the wordlists that you use. Now
Top 10 Screen Sharing Apps For Mac OS
In the age of remote work, professionals are transforming their workspaces from offices to homes. Virtual connectivity, presentations, and interactive team sessions have become integral to maintaining workflow consistency. Screen sharing applications play a vital role in delivering effective presentations
Top 10 Android Emulators
Emulators have become indispensable for those seeking a bridge between Android and their computers. Whether you’re a mobile gamer, an app developer, or just someone who prefers the versatility of their PC, Android emulators have you covered? In this list,
Top 10 Android Cleaning Apps
Are you grappling with frequent storage issues, a slower device, or excessive heat? Maintaining your smartphone might be the key to resolving these problems. If you find yourself clueless about smartphone maintenance, worry not! Android cleaning apps are here to
Top 10 Cleaning Apps for MACs
Our PCs work hard to deliver the best outputs, but with the constant use of data, they can accumulate a pile of junk and unwanted files, slowing down the system. To tackle this issue, various disk cleaner software has been
Top 10 Vulnerable Operating Systems
In the world of cybersecurity, hands-on experience is crucial for mastering the art of protecting systems. Virtual Machines (VMs) provide a safe environment for enthusiasts to practice penetration testing and explore various hacking techniques. In this article, we’ll delve into
Top 10 VPN for iOS
In a world where data vulnerability is a real concern, Virtual Private Networks (VPNs) have become essential for ensuring protection, security, and privacy. If you own an iOS device, here’s a comprehensive list of the top 10 VPNs that can
Top 10 Secure Messaging Services For iOS
In a world where data privacy is paramount, securing your messages against cyber threats has become crucial. This article explores the top 10 secure messaging services for iOS that employ end-to-end encryption, ensuring worry-free communication with your friends and family.
Top 10 Secure Messaging Services For Android
In this article, we delve into the realm of secure messaging services for Android, employing end-to-end encryption to shield your text messages and chats from third-party interceptions and cyber-attacks. Let’s explore the top 10 services that ensure worry-free communication on
Top 10 paid Vulnerability Scanner
Vulnerability scanning software is a crucial tool in the world of cybersecurity. It helps identify weaknesses in systems, providing analytical reports on their performance against known vulnerabilities. In this article, we present the top 10 paid vulnerability scanners, offering a

How to Hack Wi-Fi using PMKID Attack:
The article is only for educational purposes and should be used for improving security of your own network. We will not be responsible for any rules that you might break in your area/country. If you agree, keep reading this article
Top 10 Paid Security Apps For iOS
In this article, we explore the top 10 paid security apps for iOS, ensuring your iPhone stays protected from viruses, and malware, and offering an array of privacy and anti-theft features for worry-free usage. iOS, developed by Apple, powers iPhones,
Top 10 Paid Security Apps For Android
In this article, we’ll explore the top 10 paid security apps for Android that ensure effective protection against viruses, malware, and provide privacy and anti-theft features, offering worry-free usage of your device. Android, Google’s mobile operating system, launched in 2008,

Top 10 Operating Systems for Hackers
Hacker’s requirement for a computer is very different from that of others. To run heavy programs, software, and hacker tools they obviously need good hardware like GPU, CPU, ram, etc. However, the Operating System is also a requirement for hackers

Top 10 most dangerous hackers in the world
We always say there are two types of people in this world with different contexts however, in the world of cybercrime and technology there are white hat hackers and black hat hackers. Though few have earned the title of most
Top 10 Free Vulnerability Scanners
In a world increasingly dependent on digital infrastructure, securing your networks and systems is paramount. Vulnerability scanning software plays a crucial role in identifying potential weaknesses and fortifying your defenses. While many organizations invest in premium solutions, there are excellent
Top 10 Firewall Apps For Android
In the vast world of Android, securing your device is paramount to ensure a smooth and safe user experience. With the ever-growing threat of viruses and malware, having a reliable firewall app becomes crucial. In this article, we will explore
Top 10 Encryption Software For Windows
In this digital era, securing your sensitive data is of utmost importance. With Windows being the dominant operating system globally, it’s crucial to explore encryption tools that offer robust protection against unauthorized access. In this article, we’ll dive into the
Top 10 Arduino Simulators For Windows
In this article, we delve into the world of Arduino simulators, providing insights into the top 10 options for Windows. These simulators offer a smooth experience for both budding and professional circuit designers, allowing them to experiment without the fear
5 Best Study Tips For Cisco CCNA Certification Exam Preparation
It’s not news to you that the Implementing and Administering Cisco CCNA Certification Solutions exam also known as 200-301 CCNA covers the fundamental networking knowledge you’ll need to get your networking career off the ground, is it? So, network foundations,
Top 10 Antivirus Security Software for iOS
In a world filled with viruses, digital protection is crucial. Installing antivirus security software is the first line of defense against potential threats to your iOS devices. Here’s a list of the Top 10 Antivirus Software for iOS, ensuring your
Top 10 Encryption Software For macOS
In a world where digital threats loom, securing your sensitive data on macOS becomes paramount. With macOS holding an 18% share in the desktop OS market, it’s crucial to fortify your files. In this article, we present the top 10

Top 10 Skills Every Hacker Must Learn
A white-hat hacker has an interesting way to explore the security field. We have seen many movies illustrating a hacker as smart, efficient, and quick enough to breach the security of big organizations. Well, it might be easy to portray

Best gadgets for your hacking Inventory
Do you ever watch a hacker in a movie and wonder how amazingly he uses various gadgets and tools to find loopholes in various systems and hack them? Well those things are present in the real world also (though not

How to Detect Hidden Wi-Fi using NetSpot
I am sure that if you are reading this article, you need to find all the wireless networks that are being broadcast in your area, including those that have hidden their SSID. So first you must know that what is

25 Best Hacking Apps for Android [2021 Updated]
Hacking apps are one the most searched term and yet there are not satisfying results on the web or on google play (android application). So, today we have comprehended the list of top 25 hacking android apps that every hacker

15 Best Hacking Books for Hackers
I’ve always received questions about my recommendations for hacking books, specifically ethical hacking and penetration testing. Below, you’ll find a list of the books I recommend. Enjoy these hacking audiobooks. I’ve compiled a list of the top 13 hacking books
20 Ways to Access Blocked Websites
Picture this scenario: You’ve just secured a lightning-fast Wi-Fi connection, excited to dive into the vast expanse of the internet. Yet, just as you attempt to access certain sites, you’re met with a discouraging “Access Denied” message. Whether it’s due

How to Get Paid Apps for Free (20 Latest Methods)
PAID APPS FOR FREE? Now, as I have your attention, let’s get on to the most awaited topic. And, the answer is yes, this article covers the top 20 ways for getting premium apps for free and Google Play Store

13 Best Websites for getting Fake Temp Email Accounts
Imagine if you can get a fake email address or fake email accounts for temporary use or short-time application without creating a new one. An infinite army of free emails for you to use as per your convenience. Wouldn`t that

30 Websites to Get Personal Information of Anyone
PERSONAL INFORMATION LOOKUP SITES Have you ever wondered how easy it is to find all your private information scattered on the net..?? How easy it is to get all your personal information…?? Just imagine my surprise when I found out

How to Unlock and Recover Android Phone
Do you want to learn how hackers hack Android phones or methods to hack Android Phones? Specifically their pattern and pin locks then you have come to the right place. Or, have you forgotten your password and are unable to

How To Hack Google Dinosaur Game
Hello guys, In this guide, I am going to show How to hack the Google dinosaur game. All of us who have ever used Chrome are familiar with Google’s infamous dinosaur game that appears when the internet goes down. It’s

How to stay anonymous and untraceable on the internet
How do Hackers stay Anonymous and untraceable while hacking? This is the most commonly asked question and rightly so. To be completely anonymous and one has to do a lot of research and hard work to truly anonymize themselves change
How to Recover and secure your Facebook Account from Hackers
Imagine chilling on a Sunday afternoon, and suddenly you get a text from a buddy (an angry one at that) accusing you of flirting with his girl on Facebook. But you never opened Facebook. And then you realize that your

Top 30 sites to get Fake phone numbers for OTP and calls
Are you a novice in hacking? If not then you would know that many of the hacking executions need a temporary phone number or alternate phone number or simply say fake phone numbers to stay out of possible trouble. You

How Hackers Hack Phone Using SMS
There are numerous ways that are used by hackers all the time. Some ways are simple while some are difficult. But since lots of ways are unknown to people except hackers, these methods are used frequently. One such method is

How to Crack Winrar Passwords and Zip Passwords
If you keep forgetting your WinRAR password or you found a good zip that is password protected and you cannot open it. That could possibly be a headache for nontechnical folks.SO we have decided to make a guide on cracking

How to Recover Your Gmail Account and secure it from hackers
Many security experts warn us about the dangers of not changing passwords frequently. The reason being that it makes it harder for hackers to hack into our accounts. But, it also makes it harder for us to get into those
6 ways to Check any unknown number – Mobile number lookup
Greetings fellow sleuths! Ever wondered who that mysterious caller is? Desperate to unveil someone’s number or caller ID? Or perhaps, you just need a free mobile number lookup tool or a reliable phone number lookup website. Daily, we face a
Top 10 Voice Spoofing Websites
Greetings prank enthusiasts and mischief-makers! Have you ever dreamt of embodying the voice of your beloved characters or pulling off a side-splitting phone prank that leaves your buddies in stitches? Well, hold on to your laughter, because the world of

Top 10 Voice Spoofing Apps for Android And iOS
When it comes to injecting some fun into your phone calls by playing around with your voice, voice-changer apps step into the limelight as entertaining tools for creative endeavors and pranks. These apps serve as software applications designed to modify

Top 15 privacy tools and security service
In an era where our lives are intricately intertwined with the digital realm, safeguarding our online activities is not just a preference but a necessity. The pervasive threat of cybercrime and the continuous monitoring by various entities make it imperative

4 Ways to Reset Administrator Password on Windows 10
When safeguarding our critical data, we commonly establish a password to fortify our systems. However, if we happen to forget this robust password, resetting the administrator password for a Windows 10 installed desktop or PC becomes necessary. Resetting the administrator

How to Recover/ Track Lost Android Phone
Many of our community readers wanted to know how they could track the lost android phone or recover lost android phone. In this guide, we will show you exactly how you can use the Find my device tool to track

Top 10 Programming Languages for Hacking
Hacking is a skill which enables you to test and penetrate every digital machine present on any network. Once a great Hacker said, “Every Digital Data is Hackable“. We are not exactly fond of hacking not because we don’t like

What is Deep Web & Dark Web: Everything You Need to Know
When you hear the terms Deep Web or Dark Web, there isn’t much you know but assume that both are somewhat similar. But, it’s not. The Deep Web and Dark Web are two completely things. If you have confusion too,

What is TOR Browser & How to Set it Up
Recently, many of the organizations have installed the TOR anonymous browser on all of the Computer systems to provide anonymity for their users. Organizations are doing this so as to keep the surfing activities anonymous from the government and third-party

Top 10 Hacking Movies of All Time
Have you watched the best hacking movies of All-time? Well, you might have watched a few movies based on hacking where a good hacker turns bad and try to collapse the infrastructure. Then the main lead of the film stops

8 Physical Security Tips to Protect your Digital Devices
In an age dominated by digital devices, the omnipresent threat of theft or loss looms large, underscoring the critical need to protect our devices and the sensitive data they harbor. Imagine the fallout if your smartphone falls into the wrong

How To Check If a Link is Safe – 8 Security Tips for Verifying Links
Navigating the vast landscape of the internet can be perilous, with the constant threat of phishing links and cyber-attacks. In this guide, we’ll unravel the mystery of ensuring link safety and protecting your device from potential threats. Whether you’re questioning

How to Protect You and Your family against Sextortion and Blackmail
Every day, there is a new story or a news article about teen girls being tricked or blackmailed for obscene pictures or other such related topics. They are forced into sending compromising photos of themselves to criminals and malicious third

How to change IMEI Number (Root method)
Changing IMEI numbers for android devices is a tricky business for those who are new to the game. Many times unless you have rooted your phone you probably won’t be able to change the IMEI number for your device. Still,

How to Recover Deleted Internet History
Many times we delete chrome history or for instance any browser’s history and end up deleting important browser history that we need back. It may be some unique site that you found or just something personal to you. Many people

How to Secure & Recover WhatsApp Account from Hackers
With billions of users of WhatsApp around the Globe, WhatsApp has become a primary target for hackers since many people are not implementing complete WhatsApp Security. People often realize the importance of WhatsApp Security after getting hacked, so their efforts

How to Read deleted WhatsApp Messages – No Root required
WhatsApp has been evolving like ever and since the acquisition by Facebook, it has seen quite a lot of updates and features. One of the features that WhatsApp introduced and folks love is “Delete for Everyone“. The delete for everyone

How to Change/ Restore IMEI Number of an Android Phone without Root
IMEI numbers use to be one of the hardest things to change in your mobile device. Well not anymore. You can now easily change and restore your IMEI number without root using free-to-download play store apps. Sounds a bit too

How to Crack Windows 10 Password with Ophcrack
It is always good to protect the computer using the password, but the other truth is, it is difficult to remember the password of multiple fields, and forgetting the same is human behavior. So, if you have forgotten Windows 10

5 Best Free Apps to Root Android Phone Easily
There are many free and paid android apps available on the internet, which you can use to root your android phone. You have to follow some simple steps given in the application. The process is very simple, convenient, and fast

Top 10 iOS Jailbreaking Apps for iPhones
If you are a tech-savvy person and want to explore beyond the boundaries set by Apple, then you might be keen about knowing whether iOS can be hacked. Well although Apple ensures a very secure operating system, yet the Apple

10 Best Internet Search Engine Used by Hackers
We all use the Internet search engine in our daily life whether to search for a recipe or to complete an assignment or some other task, but have you ever wondered what kind of tools and Internet search engines hackers

13 WhatsApp Security Tips for being hack-proof – Expert Tips
Recently a lot of WhatsApp account(s) were being hacked by spyware and malicious links being spread on the internet, also some due to the WhatsApp security bug. Even though WhatsApp tries its best to keep us secure if we are

Have you been hacked? How to spot spyware and viruses on your phone
With the increase in the number of devices over the years, the number of spyware apps has also increased to a considerable extent and it is getting difficult to spot spyware apps or at least detect spyware while it is

12 reasons to avoid public Wi-fi – What’s the worse that can happen?
The word free Wi-Fi makes everyone happy. But the reality is you might be getting into more trouble than what you signed up for. The main problem with public Wi-Fi is there is no security when it comes to your

How to detect bank phishing scams (12 Things banks will never do)
Recently the rise of bank phishing scams has grown to such a large extent that it is no longer possible to ignore the risks. Everyone is being targeted by spam and messages claiming to be from the bank. Hackers and

How to secure your android device from malware (11 Tips from experts)
If you are worried about online safety and want to know how to keep your device safe from malware and social engineering, Then this article is for you. At the end of this article, you will be much safer than

How to setup NOIP in Linux for managing dynamic IP address
What is NOIP? Dynamic IP addresses are a real headache for hackers and network engineers. Once the modem restarts, 99 % of the time you will be getting a new public IP address which means any hack you had previously

What are Social Engineering Attacks? Best Tips to Stay Safe
Social engineering attack is an assault vector that is based closely on human interplay and regularly involves manipulating humans into breaking ordinary security tactics and high-quality practices to be able to benefit access to structures, networks, or bodily places, or

How to create nameless blank file and blank folder in windows
Do you want to create a nameless folder or file (Blank Folders or file) and nameless files? Do u think it is possible to make such folders? The answer to this is yes, you can easily make such folders by

10 Tips to be safe online from hackers
As the new year dawns, the threat of hacks and viruses looms large. Arm yourself against cyber threats with these easy steps to stay safe online, irrespective of your device. 1. You’re a Possible Target {#deny-target} Dismiss the notion that

How to Hack a PDF File Password on Windows
What if you have an old password-protected PDF file that you need and whose password you have forgotten? Is there any way to hack or crack the pdf file password and get access to the pdf file. Well, no need

8 Ways To Secure iPhone and MacBook Device In 2021
In our fast-paced digital world, ensuring the security of your iPhone and MacBook is paramount. From protecting personal data to preventing unauthorized access, this comprehensive guide explores eight essential ways to bolster the security of your Apple devices. Whether you’re

Top 10 Sites to Unshorten Shortened URLs
In the ever-evolving landscape of the internet, we’ve all encountered URLs—those strings of characters that lead us to various corners of the web. However, the simplicity of URLs can be deceiving, especially when it comes to shortened links. Understanding the

How to View Any Saved WiFi Passwords in Windows 10
Its quite common for us to forget the network password since most of the time, our computers and laptops automatically connect to our Wi-Fi networks, and the same can be said with our smartphones. is your smartphone. The autocorrect feature

Top 10 Best Bug Bounty Platforms to Earn Money Online
Application security is a field that will always be in the limelight when we talk about Computer Science. Today hacking has become so prominent that only a hacker can defeat a hacker. Many corporations invite hackers through bug bounty programs

Top 5 Secure Email Services You Should Use
In the vast landscape of cyberspace, where information flows freely, your email account stands as a gateway to your digital world. Yet, with great convenience comes great vulnerability. The prevalence of cyber threats demands a reevaluation of our email practices,

How to Secure Your Account From Hackers [In-depth guide 2021]
Welcome fellow hackers, are you now scared seeing how easy it is to hack passwords…?? Well, fear not, we have made a comprehensive guide just for you to ensure you always have a secure account and hackers could not get

How to Secure Yourself From Hackers in 2021
As technology is updating at a rapid rate, even cyber crimes have been increasing day by day. The rate of hacking, stealing, cyber frauds, bank scams, etc has been increasing daily. There is a need to be on the internet nowadays.

How to do port forwarding manually without a software
There is much software for port forwardings such as Ngrok and NOIP. But not everyone prefers using software for port forwarding. So here is a manual method of port forwarding and hacking over the internet by using your public IP.

How to Hide Data Files in Images using Steghide & Kali Linux
Steganography is a technique used to hide files and sensitive data inside an image so that it can be transported without arousing any suspicion. It is mostly used for Blackhat Hacking. It is generally encrypted so that data remains secure.

How to setup NOIP for Updating dynamic IP on windows
This is how you can set up NOIP for Updating dynamic IP on windows. Similar to ngrok there are many alternatives for port forwarding tools on the internet. One such tool is NOIP. If you have a hack that you

How to setup Ngrok for port forwarding without router
Hey guys, due to popular demand we are going to make this guide to port forwarding. This guide can help you port forward your IP so that you can perform hacks over the internet. We will do Port forwarding with

How to install Kali Nethunter on android – A step by step guide
In many of my previous tutorials, I suggested installing Kali Linux nethunter on your android devices. Well, unfortunately, many people were having a lot of difficulty with it. So today we are going to a very special tutorial on how

How to install Kali Linux on android with termux without root
Today we will show you how to install kali Linux on android using termux without root. Many people do not like rooting their android phones for numerous reasons starting from security to the warranty of their devices. In some cases,

How to Reverse trace emails on the internet – Complete Guide
Are you worried about spam or probably malicious inquiry by someone pretending to be your client? There fear not we are here to help you find the truth. Many times you will get fake emails asking for compensation or claiming

Hacking With Shodan (How to use Shodan Guide)
Today we are reviewing shodan also know as the hacker’s search engine. We will see what shodan is and how to use shodan. We will also explore some advanced features of shodan. Everything related to shodan search filters and shodan

20 Best Websites to Learn Ethical Hacking for Beginners
When someone asks me about the best websites to learn hacking or ethical hacking, I suggest lots of websites according to their choice and skills. But that demands quite a work to know each individual and suggest them accordingly, so

How to Extract Password from password hashes with Johnny
If you have already read my article on john the ripper you know how hackers can hack passwords provided they can get access to the password hashes. Now I hope you know how to get password hashes or least what

How to Extract Password Hashes using Windows & Linux OS
I did many tutorials on cracking passwords, but no one seems to know how to extract password hashes. Well on popular demand we have decided to make an in-depth tutorial on extracting password hashes so that we can hack them

How to extract password from password hashes on android- Hash suite droid
If you want to do a password cracking attack but do not have a laptop or a pc then no worries you can now how crack passwords using your android phone. Now we have hash suite droid the password cracking

How to hack passwords with john the ripper (linux, zip, rar, hash)
Today we are going to learn how to crack passwords with john the ripper. If you have never heard about it, then you are surely missing a lot of passwords cracking action. John, the ripper, is an open-source password cracking